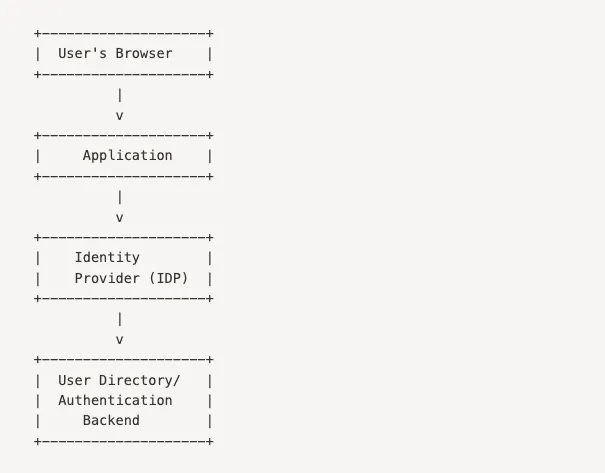
Single Sign-On (SSO): Potential flaws or vulnerabilities in the implementation
The blog post explores the potential flaws and vulnerabilities in the implementation of Single Sign-On (SSO) systems.
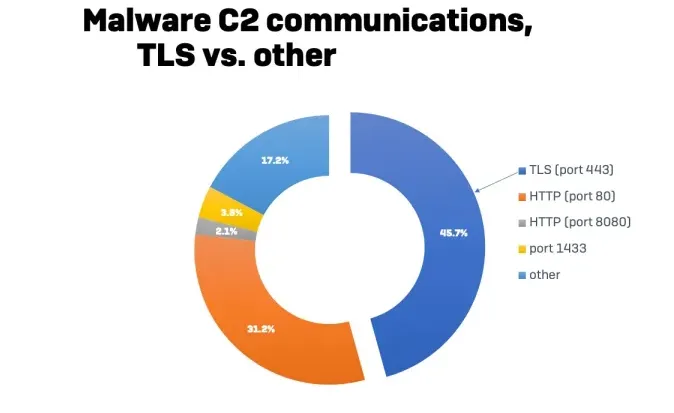
Encrypting Communications in Malware: A Dive into Windows API Functions with Python
The blog post explores how to encrypt communications in malware using Windows API functions and Python.
Secrets Management: What to use Env variables or Vault?
The blog post is about secrets management and discusses the pros and cons of using environment variables versus using a tool like Vault.
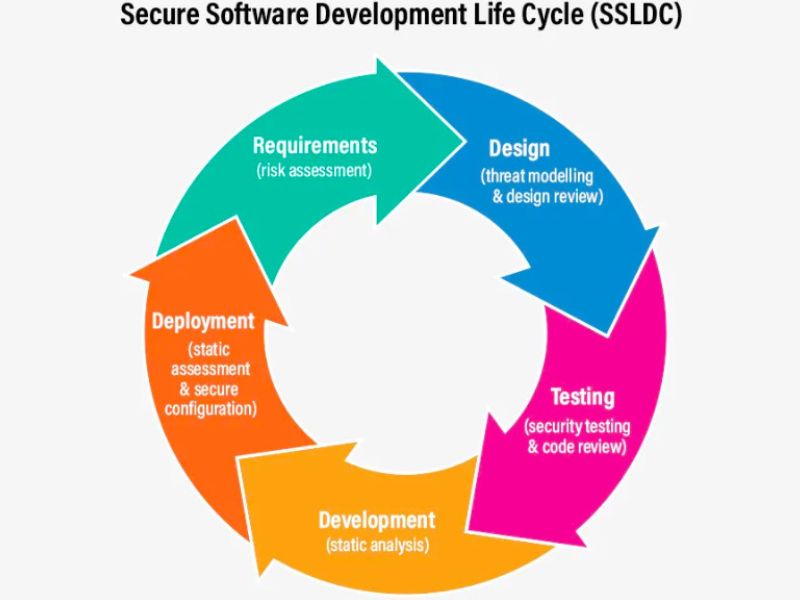
What does it mean building a secure software ?
The blog post discusses what it means to build a secure software and why it is important. The author highlights the need for a security-first mindset and lays out the key principles for building secure software.
Secure code review process in 4 steps
The blog post titled "Secure Code Review Process in 4 Steps" outlines a four-step process for conducting secure code reviews.